How did the Enigma encryption machine work and is it used today?
How did the Enigma encryption machine work and is it used today?
In ancient times, the method of hiding secret information was simply writing. There were very few literate people, so the more educated could simply write messages on sheets of paper – most people simply were not capable of reading them. But as time went on, people became more literate and the need for sophisticated encryption systems arose. At first, people, especially the military, masked important data by substituting letters of the alphabet. For example, in 100 B.C. Caesar’s cipher was popular – each letter in the original text was replaced by another letter, which stands in the alphabet after a certain number of positions.
Around the twentieth century, the first devices began to appear that replaced some symbols with others automatically. The most famous of these was the Enigma.

The inventor of the Enigma is considered to be the German engineer Arthur Scherbius. In the early stages of his career he created asynchronous motors, electric pads, ceramic heating parts, and other electronic devices. In 1918, he applied for a patent for the Enigma encryption machine, which looked like a 50-pound cash register. He later created improved versions that became more portable – they were comparable in size to typewriters. At first, the device for encrypting secret messages was not in demand, but in 1926 the German Navy became interested in it. This moment can be considered the beginning of the use of Enigma in the military.
The fact that the encryption machine came in handy in the military sphere is not surprising. Concealment of information has always been a necessary condition for successful warfare. Thanks to ciphers, military units and commanders could constantly keep in touch. Even if data was intercepted by enemy forces, it was useless because only those who knew how to decipher it could read it.
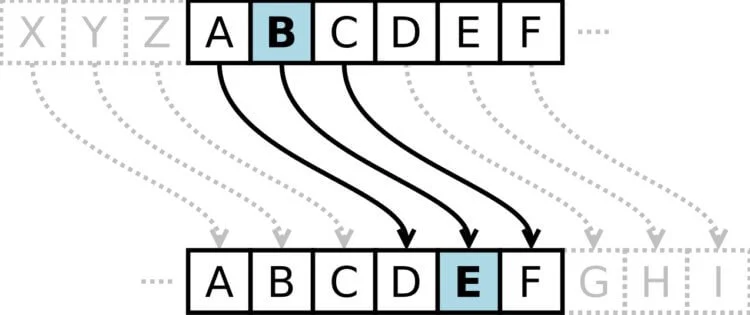
The text to be encrypted was printed directly on the Enigma. Before using it, the operator opened the lid of the machine and memorized the setting position – the three numbers that would later be needed to decipher the message. After that, a secret text was written, in which each character was changed to a different one, making the message look like a random set of letters. The symbol-swapping mechanism had an algorithm that varied depending on the gears installed inside.

After writing the message, the author would pass the three pre-recorded numbers to the radio operator, who would send them to the recipient using Morse code. The person on the other side, who had the same Enigma, put the machine on the same setting and typed an incomprehensible set of letters on the machine. As a result of this action he received the decoded text.
The Enigma cipher was first cracked by Polish intelligence in 1932. Their work prompted the English mathematician Alan Turing to create a decryption device called “Bombe”. Breaking the encryption machine was made possible by defects in the encryption algorithms. Subsequently, Enigma was updated many times, because the developers closed all the vulnerabilities in time.
Is Enigma in use today?
In the second half of XX century there appeared full-fledged computers compared to which Enigma seems like a child’s toy. Because of this, there is no need to use the old encryption machine anymore. Some copies of Enigma are exhibits in museums of USA, Germany and other countries. If you want to at least virtually use the legendary machine, you can find online simulators of Enigma on the Internet.
Today, instead of Enigma and other mechanical machines, computer algorithms are used to encrypt information. In essence, they do the same thing as Enigma, but as quickly as possible and with the highest reliability. If it takes unattainable computer power or a very long time to decrypt a message, the encryption algorithm is considered to have maximum cryptographic strength.
It is noteworthy that algorithms to protect data are not only used in the military sphere, but also in ordinary technology that is connected to the Internet. As an example, we can take smartphones with installed messengers – every self-respecting and user-respecting developer assures that all messages go through encrypted channels. And because of this, it is virtually impossible to intercept data.
